14 Nov CMMC Requirements for Defense Contractors – Your Comprehensive Guide to CMMC 2.0, Framework, Controls, and Compliance Steps
Navigating CMMC Requirements for Defense Contractors: Understanding CMMC 2.0 and CMMC Framework Explained
Estimated reading time: 8 minutes
Key Takeaways
- Mandatory DFARS clauses make CMMC compliance a contractual requirement for all DoD contractors.
- CMMC 2.0 streamlines certification from five levels to three, aligning fully with NIST SP 800-171/172.
- Self-assessments are allowed for Level 1 and certain Level 2 contracts, reducing costs.
- Third-party C3PAO and DIBCAC assessments ensure rigorous evaluation for higher levels.
- A structured roadmap—gap analysis, remediation, pre-assessment, certification—ensures a clear path to compliance.
Table of contents
- Navigating CMMC Requirements for Defense Contractors
- Key Takeaways
- Understanding CMMC 2.0
- CMMC Framework Explained
- CMMC Requirements for Defense Contractors
- CMMC Controls and Practices
- CMMC Assessment Guidelines
- Comparing CMMC 1.0 vs. CMMC 2.0
- Roadmap to Compliance
- Conclusion and Next Steps
- Frequently Asked Questions
Understanding CMMC 2.0
The Cybersecurity Maturity Model Certification (CMMC) represents a critical shift in how the Department of Defense (DoD) protects sensitive information throughout its supply chain. As a defense contractor, understanding the CMMC requirements for defense contractors has become essential for maintaining your ability to compete for and win DoD contracts.
CMMC 2.0 represents the DoD’s revised, risk-based cybersecurity maturity model designed to safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). This updated framework significantly reduces complexity while providing greater clarity on assessment tiers.
Key changes from the original CMMC 1.0 include:
- Reduction from five certification levels to just three, creating a more focused and accessible system
- Introduction of self-assessments for Level 1 and parts of Level 2, substantially lowering compliance costs
- Full alignment with NIST SP 800-171 for Level 2 and above, with Level 3 specifically reserved for Advanced Persistent Threat (APT) defense
These changes deliver several important benefits to defense contractors:
- More scalable, risk-based controls that reduce the burden on smaller companies
- Clear delineation between self-assessment and third-party assessment requirements
- Continued emphasis on protecting the entire defense supply chain
For an in-depth legislative overview, see CMMC regulations key questions and answers for defense contractors.
CMMC Framework Explained
The CMMC framework provides a structured approach to cybersecurity through its organization of domains, practices, and processes. This architecture allows for consistent assessment of security maturity across the defense industrial base.
The framework establishes three distinct certification levels:
Level 1: Foundational
- Protects Federal Contract Information (FCI)
- Requires implementation of 15 basic cybersecurity practices
- Demands annual self-assessment by the contractor
Level 2: Advanced
- Designed to protect Controlled Unclassified Information (CUI)
- Incorporates 110 practices aligned with NIST SP 800-171
- Assessment requirements vary based on contract specifics (self-assessment or third-party C3PAO assessment)
Level 3: Expert
- Focused on defending against Advanced Persistent Threats (APTs)
- Builds on Level 2 controls by adding requirements from NIST SP 800-172
- Requires DoD-led DIBCAC assessment exclusively
This structured approach allows defense contractors to clearly understand what protections they need to implement based on the sensitivity of the information they handle in DoD contracts.
CMMC Requirements for Defense Contractors
CMMC requirements for defense contractors are now formalized through mandatory DFARS clauses that directly affect contract eligibility. Specifically, these obligations appear in DFARS clauses 252.204-7021 and 252.204-7025, which establish cybersecurity as a fundamental requirement for doing business with the DoD.
Contractual Mandates
- Register in the Supplier Performance Risk System (SPRS)
- Post the appropriate certification level in SPRS before contract award
- Maintain continuous compliance with all applicable CMMC requirements throughout the contract period
DFARS Obligations and Flow-Down Requirements
- Clause 252.204-7021 requires notification of non-compliance within 30 days of discovery
- Clause 252.204-7025 details specific CUI protection requirements based on certification level
- Prime contractors must ensure that all subcontractors achieve and maintain the required CMMC level
See detailed analysis from Department of Defense releases long-awaited DFARS cybersecurity final rule for government contractors and subcontractors.
The flow-down requirement creates a cascading compliance obligation throughout the defense industrial base.
CMMC Controls and Practices
CMMC controls and practices form the technical backbone of the certification framework. Each level includes specific security measures designed to address increasingly sophisticated threats.
Level 1 Controls
- Implementation of unique user identification systems
- Establishing basic device access restrictions
- Creating incident reporting procedures
- Implementing basic physical security measures
- Performing regular backup of critical system information
Level 2 Controls
Technical requirements:
- Multifactor authentication implementation (3.5.3)
- Data-at-rest encryption (3.13.11)
- Network boundary protection
- Audit logging and review
Procedural requirements:
- Formal incident response planning (3.6.1)
- Regular risk assessments (3.11.1)
- Security awareness training
- Configuration management processes
Level 3 Controls
- Enhanced threat detection controls from NIST SP 800-172
- Advanced network monitoring and response capabilities
- Rigorous vulnerability management and continuous diagnostics
For deeper analysis, see Key takeaways for defense contractors and what to expect when the new CMMC final rule hits defense acquisitions on November 10.
CMMC Assessment Guidelines
CMMC assessment guidelines establish clear processes for evaluating compliance, with assessment types varying by certification level and contract requirements.
Assessment Types
- Level 1: Annual self-assessment, results published in SPRS, no third-party verification
- Level 2: Certified Third-Party Assessment Organization (C3PAO) or self-assessment where allowed
- Level 3: Government-led DIBCAC assessment, the most rigorous tier
Scoring Methodology and Evidence Requirements
Assessments use a weighted scoring approach categorizing each practice as fully implemented, partially implemented, or not implemented. Contractors must provide formal policies, system configuration screenshots, security logs, and training records. Identified deficiencies are documented in Plans of Action and Milestones (POAMs) with timelines for closure.
Timeline and Cost Expectations
The DoD is implementing a phased rollout through 2028. Level 1 self-assessments represent the lowest cost, C3PAO assessments for Level 2 incur moderate fees, and DIBCAC assessments for Level 3 are the highest cost tier. Organizations should budget for initial certification and ongoing compliance maintenance.
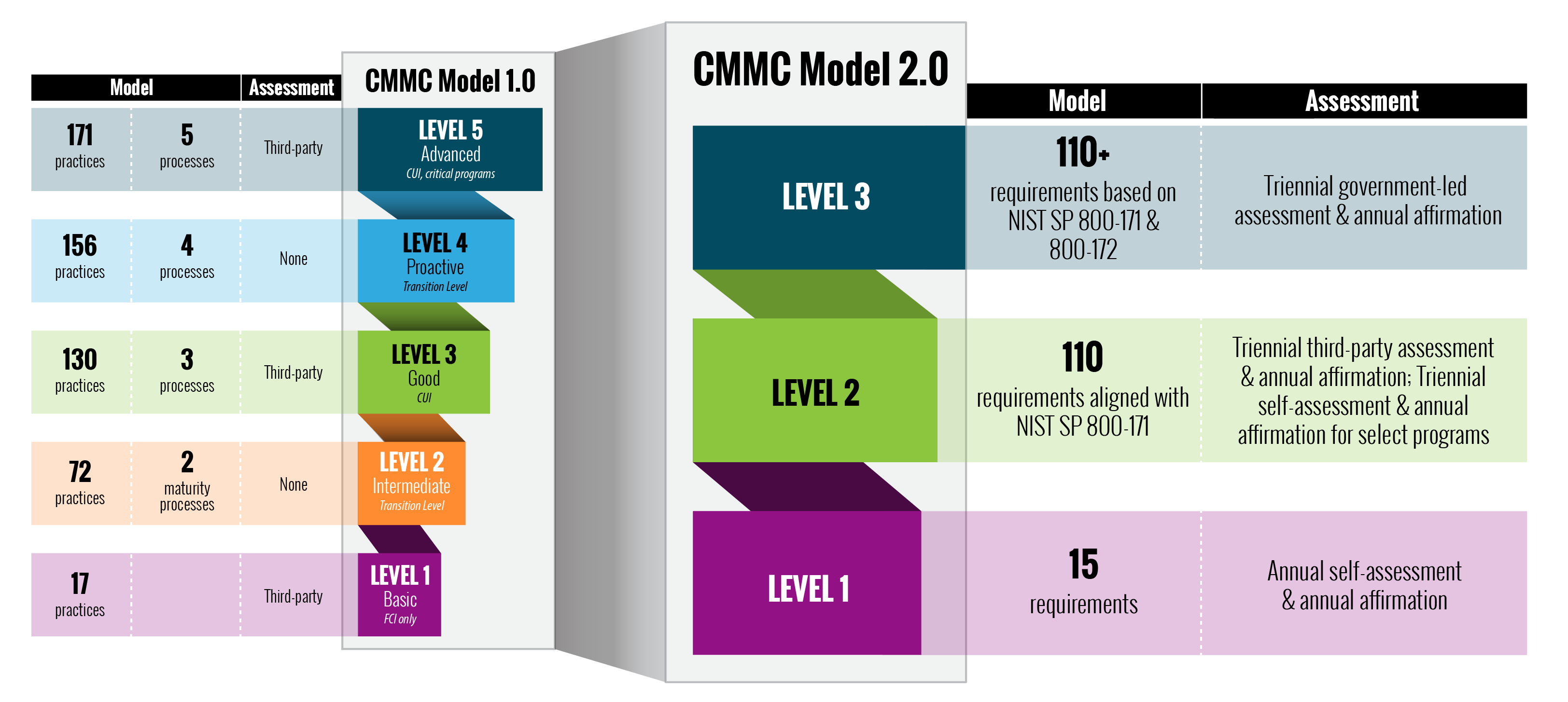
Comparing CMMC 1.0 vs. CMMC 2.0
Understanding the evolution from CMMC 1.0 to CMMC 2.0 highlights the streamlined approach now available to contractors.
Side-by-Side Comparison
- Certification Levels: CMMC 1.0 featured five levels; CMMC 2.0 streamlines to three
- Assessment Requirements: CMMC 1.0 required third-party assessment at all levels; CMMC 2.0 introduces self-assessment options
- NIST Alignment: CMMC 1.0 had partial alignment; CMMC 2.0 achieves full alignment with NIST SP 800-171/172
- Compliance Burden: CMMC 1.0 imposed higher complexity and cost; CMMC 2.0 reduces burden, especially for smaller contractors
Pros and Cons Analysis
- CMMC 1.0: Detailed maturity progression but complex and costly
- CMMC 2.0: Simpler, cost-effective, clearer NIST alignment but requires detailed self-assessment documentation
Version Recommendations by Contractor Maturity
- Small firms: Level 1 or limited Level 2 under CMMC 2.0 for cost-effectiveness
- Medium-sized contractors: Level 2 under CMMC 2.0 balances security and cost
- Large/CUI-centric contractors: Level 2/3 under CMMC 2.0 for comprehensive protection
Roadmap to Compliance
Achieving CMMC compliance requires a methodical approach. Follow this proven roadmap to navigate the certification process effectively.
Step 1: Gap Analysis
- Utilize NIST SP 800-171/172 crosswalk tools to inventory existing controls
- Document current policies, procedures, and technical implementations
- Identify gaps between current state and required controls
- Prioritize gaps based on risk and implementation complexity
Step 2: Remediation
- Develop missing policies and procedures for access control, incident response, and other domains
- Implement technical solutions including MFA, encryption, and network monitoring
- Document standard operating procedures for all security practices
- Maintain evidence of implementation throughout the remediation process
Step 3: Pre-Assessment
- Perform an internal audit against the required control set
- Compile comprehensive evidence including screenshots, logs, and training records
- Verify documentation completeness and policy implementation
- Address remaining gaps before formal evaluation
Step 4: Certification
- Level 1: Upload self-assessment results to SPRS
- Level 2: Engage a C3PAO or complete a self-assessment as required
- Level 3: Prepare for a DIBCAC assessment
- Address any POAMs quickly to maintain compliance
Tools and Resources
- DoD CMMC portal
- DoD CIO CMMC overview
- SPRS portal for certification reporting
- POAM templates for tracking remediation
Conclusion and Next Steps
CMMC requirements for defense contractors represent a significant evolution in how the DoD secures its supply chain. The streamlined CMMC 2.0 framework offers a more focused, risk-based approach to certification, ensuring robust security while reducing complexity.
Actionable Next Steps
- Begin a gap analysis to assess your current security posture
- Engage a C3PAO for Level 2 readiness evaluation if required
- Prepare for a DIBCAC assessment for Level 3 certification
- Train staff and document policies thoroughly
- Upload SPRS scores and maintain continuous compliance
Frequently Asked Questions
What is the difference between CMMC 2.0 Level 1, Level 2, and Level 3?
CMMC 2.0 Level 1 focuses on basic protection for Federal Contract Information (FCI) with 15 foundational practices and annual self-assessment. Level 2 aligns fully with NIST SP 800-171 and requires 110 practices, with either self-assessment or third-party evaluation. Level 3 adds advanced controls from NIST SP 800-172 and necessitates a DoD-led DIBCAC assessment.
How do I prepare for a CMMC assessment?
Begin with a gap analysis against the CMMC control set. Develop missing policies and implement required technical solutions. Conduct a pre-assessment to verify evidence completeness. Finally, engage the appropriate assessment body—self-assessment, C3PAO, or DIBCAC—based on your target level.
What are the costs associated with CMMC certification?
- Level 1: Low cost for annual self-assessments
- Level 2: Moderate cost for C3PAO assessments; lower cost when self-assessment applies
- Level 3: Highest cost due to government-led DIBCAC evaluations
How often must I recertify or reassess?
Level 1 and applicable Level 2 self-assessments must be completed annually. Third-party assessments for Level 2 and DIBCAC evaluations for Level 3 follow DoD-specified schedules, typically every three years or per contract requirements.
How do DFARS clauses impact subcontractors?
DFARS clauses 252.204-7021 and 252.204-7025 require prime contractors to flow down CMMC requirements. Subcontractors must register in SPRS, achieve the required certification level, and maintain continuous compliance to remain eligible for DoD work.


